Overview of Cybercrime
Definition of Cybercrime
Cybercrime refers to criminal activities that are conducted through the internet or with the aid of computer systems. It represents a diverse range of offenses targeting various sectors—individuals, organizations, and governments alike. The rise of the digital age has exponentially increased the opportunities for perpetrators, leading to innovative methods of committing crimes. To put it simply, cybercrime can be seen as a modern-day equivalent of traditional crime, but instead of physical confrontation, it relies on technology and the internet. Here are some key characteristics that define cybercrime:
- Utilization of Technology: Cybercriminals leverage technology to exploit or attack their victims, and this can include anything from phishing emails to sophisticated hacking techniques.
- Anonymity: One of the appealing aspects of cybercrime for criminals is the veil of anonymity that the internet provides. Many offenders go undetected precisely because of their ability to obscure their identities.
- Global Reach: Unlike traditional crimes that are often restricted by geographical boundaries, cybercrimes can cross borders with utter ease, rendering it challenging for law enforcement agencies to address these crimes effectively.
Given this definition, it's crucial to understand the broader implications of cybercrime in our lives as we increasingly interface with technology in our day-to-day activities.
History and Evolution
While the term "cybercrime" may seem modern, its roots trace back several decades. The evolution of cybercrime is marked by technological advancements, societal changes, and legal developments.
- 1970s and 1980s: The first instances of cybercrime emerged with the advent of computers. As early as the 1970s, individuals began experimenting with computer networks, and opportunistic hackers started to emerge, illicitly accessing systems for amusement or to demonstrate their skills. In 1986, the U.S. Computer Fraud and Abuse Act was enacted, marking one of the first legislative attempts to address computer crimes.
- 1990s: The 1990s saw the introduction of the World Wide Web, which expanded the landscape of potential cybercrimes. Notable offenses included the spread of computer viruses, the first major cases of online fraud, and the rise of hacking communities, which shared techniques and knowledge that fueled further criminal activity.
- 2000s to present: With the rise of social media, smartphones, and e-commerce, new types of cybercrime have emerged, such as identity theft and phishing. High-profile data breaches, like the one involving Target in 2013, demonstrated the vulnerability of even the most prominent corporations. More recently, ransomware attacks have become a lucrative business for cybercriminals, affecting hospitals, municipalities, and private enterprises.
Reflecting on this history provides a clearer picture of how cybercrime has transformed alongside technology. Each advancement brings new opportunities for criminal activities, leading to a continual game of cat-and-mouse between cybercriminals and cybersecurity professionals.
Personal Anecdote
Take the story of a small business owner, Lisa, who faced a phishing attack. Unsuspecting of the dangers lurking online, she clicked on a link in an email that appeared to be from her bank. In seconds, her personal and business information was compromised, leading to financial loss and stress. Lisa's experience is a symptom of a broader epidemic that highlights the need for robust cybersecurity measures in today’s digital world.
In Summary
The definition and historical context of cybercrime illustrate how much it has evolved with the times. From simple computer hacking in the early days to sophisticated attacks that leverage massive data breaches, understanding its origins allows individuals and organizations to be better prepared. As technology continues to evolve, so too will the methods and motivations behind cybercrime, making vigilance an essential part of our digital lives.

Types of Cybercrimes
As the digital landscape continues to evolve, so too does the breadth of cybercrimes that can affect individuals and organizations. Each type of cybercrime poses unique challenges and consequences, demanding awareness and protective measures. Let's explore some of the most prevalent types of cybercrimes today.
Identity Theft
Identity theft occurs when someone unlawfully obtains and uses an individual's personal information, typically for financial gain. This crime can happen in numerous ways, including hacking, data breaches, and phishing. When an identity thief gains access to sensitive information such as Social Security numbers, bank account details, or credit card information, they can wreak havoc on the victim's financial standing and personal life.
- Personal Anecdote: Consider the story of Tom, who received a call from his bank's fraud department about suspicious activity on his credit card. After some investigation, it turned out that his identity had been stolen, resulting in unauthorized purchases that drained his savings. The emotional and financial fallout was immense, illustrating just how serious identity theft can be.
Victims of identity theft often face significant long-term challenges, including restoring their credit ratings and managing the fallout from fraudulent transactions. It typically requires substantial time and effort to rectify the damage caused by this type of crime.
Phishing Attacks
Phishing attacks are one of the most common and insidious forms of cybercrime. Criminals use deceptive emails or messages that appear to be from reputable sources to trick individuals into revealing sensitive information, such as login credentials or financial information. These attacks often create a sense of urgency or fear to compel victims to act quickly without careful consideration.
- Examples of Phishing Tactics:
- Email Scams: An email claiming to be from your bank, asking you to confirm your account details.
- Fake Social Media Messages: A message from a "friend" requesting your login information, indicating they’re locked out of their account.
The impact of falling victim to a phishing attack can be devastating. Victims not only risk financial loss but also the potential compromise of their personal and professional reputations.
Malware Distribution
Malware, short for malicious software, encompasses a range of harmful software designed to damage, disrupt, or gain unauthorized access to computer systems. Distribution of malware can take many forms, from trojans and worms to spyware and adware. Cybercriminals can deliver malware via email attachments, infected downloads, or compromised websites. Key points about malware distribution include:
- Types of Malware:
- Trojans: Disguised as legitimate software but harmful once installed.
- Worms: Self-replicating malware that spreads across networks without human intervention.
- Spyware: Software that secretly monitors user behavior and collects sensitive data.
A personal story to illustrate the seriousness of malware—imagine a small business owner named Sarah, who unknowingly downloaded a malware-infected file while trying to access a free software tool. Her entire network was infected, leading to lost data, downtime, and expensive recovery efforts.
Ransomware
Ransomware is a particularly alarming form of cybercrime where malicious actors encrypt a victim's files or lock their systems and demand a ransom for restoration. This class of attacks has gained notoriety due to its severe impact on both individuals and organizations.
- Key Features of Ransomware:
- Encryption: Files are rendered inaccessible until a ransom is paid.
- Extortion: Attackers often demand payment in cryptocurrencies to obscure their identities.
The ramifications of a successful ransomware attack can be catastrophic. Organizations may face extortion, data loss, and reputational damage, while individuals can suffer from the loss of personal files and precious memories.
In Summary
Understanding the different types of cybercrimes is essential for navigating today’s digital terrain safely. From identity theft to phishing, malware distribution, and ransomware, each has unique characteristics and consequences. Being informed about these threats is the first step in developing effective strategies for prevention and protection. As the cybercrime landscape evolves, so must our awareness and response mechanisms to safeguard ourselves and our communities.
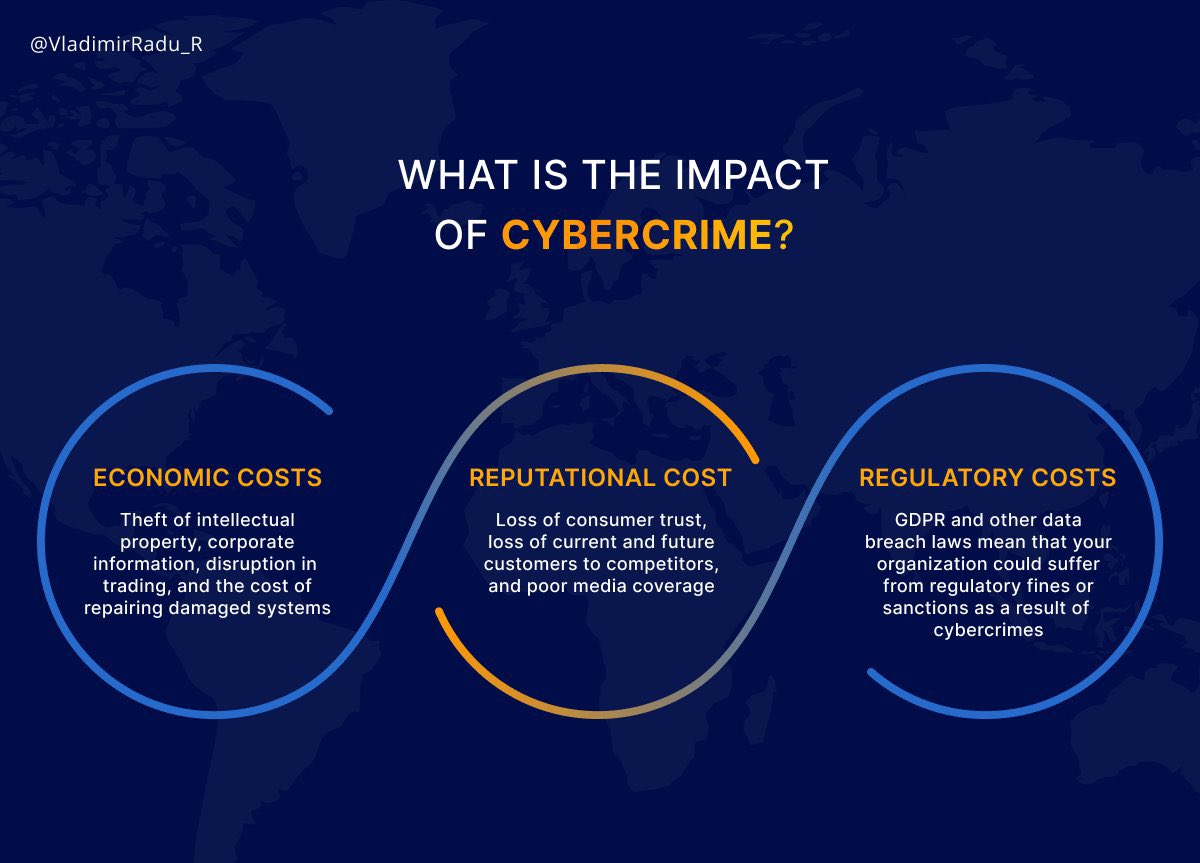
Impact of Cybercrime
The repercussions of cybercrime are far-reaching, affecting not only the immediate victims but also the broader societal landscape. This section will delve into three major impacts of cybercrime: financial losses, reputational damage, and legal consequences.
Financial Losses
Financial losses from cybercrime can be staggering, often reaching into millions or even billions of dollars. The sophistication of the attacks and the different methods employed by cybercriminals can lead to widespread financial repercussions for individuals and organizations alike.
- Examples of Financial Losses:
- Direct Theft: Cybercriminals often steal funds directly from bank accounts or initiate fraudulent purchases, leading to direct financial hits for individuals and businesses.
- Cost of Recovery: Organizations hit by cyberattacks must spend heavily on recovery efforts. This may include hiring cybersecurity experts to investigate breaches, restoring compromised data, and enhancing security measures to prevent future incidents.
- Business Interruption: A successful cyberattack can disrupt normal business operations, leading to lost revenues. For instance, when ransomware strikes, companies might be forced to go offline until the threat is resolved.
Take the instance of a major retail chain that fell victim to a data breach. They had to spend millions not only rectifying the breach but also compensating affected customers. The financial burden went beyond immediate damages, affecting their long-term profitability.
Reputational Damage
Cybercrime inflicts significant reputational damage. Once trust is broken, it can take years to rebuild, resulting in lost customers and diminished brand loyalty. For businesses, a tarnished reputation can be more damaging than the actual financial losses incurred from a cyber incident.
- Key Factors in Reputational Damage:
- Customer Trust: Customers expect their data to remain secure. When a breach occurs, many may choose to take their business elsewhere. The loss of trust is exacerbated in the age of social media, where negative news travels quickly.
- Public Perception: Companies struggling with their cybersecurity can find themselves in a difficult position publicly. A data breach may be perceived as a sign of weakness or negligence, further alienating potential customers.
Consider the case of a well-known hotel chain that experienced a significant data breach affecting millions of guests. The aftermath was an avalanche of negative media coverage. Many loyal customers felt betrayed and opted for alternative accommodations, resulting in millions in lost business—something from which they struggled to recover for years.
Legal Consequences
The legal ramifications of cybercrime are extensive and can lead to serious consequences for both the perpetrators and the victimized organizations. As laws surrounding cybersecurity tighten globally, organizations that fail to comply face substantial penalties.
- Consequences for Organizations:
- Regulatory Fines: Organizations that suffer a breach may be subject to fines from regulatory bodies, especially if it is determined that they did not take the necessary precautions to protect their data.
- Lawsuits: Victims of identity theft or data breaches may file lawsuits against organizations for negligence, leading to costly legal battles and settlements.
For example, healthcare organizations are mandated to protect patient data under regulations such as HIPAA. When breaches occur, they face severe fines and even criminal charges for exposing sensitive data. In addition to financial penalties, the legal fallout can result in a loss of trust from clients and customers, hindering growth and sustainability in a competitive marketplace.
In Summary
The impacts of cybercrime are profound and multifaceted, stretching beyond finances to reputation and legal obligations. As demonstrated through personal anecdotes and real-world examples, the consequences can devastate businesses and affect individuals significantly. As we move forward, understanding these impacts is crucial for individuals and organizations alike, enabling them to take proactive steps to mitigate risks and safeguard their valuable assets in an increasingly complex digital environment.

Cybercrime Prevention
Preventing cybercrime is essential in today's world, where the consequences can be devastating both financially and reputationally. Fortunately, organizations and individuals can take various proactive steps to safeguard their information and systems. This section will explore three significant strategies for cybercrime prevention: using strong passwords and encryption, keeping software updated, and implementing employee training.
Strong Passwords and Encryption
The foundation of securing sensitive information starts with robust passwords and encryption. Weaknesses in this area often create vulnerabilities that cybercriminals can exploit.
- Strong Password Practices:
- Complexity: A strong password typically includes a mix of upper and lower case letters, numbers, and special characters. Avoid common words or phrases.
- Length: Aim for at least 12 characters. Longer passwords contribute significantly to security.
- Unique Passwords: Each account should have a unique password to prevent a single breach from compromising multiple accounts.
- Using a Password Manager: Tools like password managers can help generate and store complex passwords securely. This way, one doesn't have to remember every single password but can still ensure that they are strong and distinctive.
- Encryption: Encrypting sensitive data ensures that even if hackers gain access, they cannot read the information without the decryption key. Using encryption for emails, files, and even entire databases adds an extra layer of security.
Personal Anecdote: Sarah, a small business owner, realized the importance of strong passwords after her email account was hacked due to a simple password. By switching to a password manager, she strengthened her security and safeguarded her business communications.
Software Updates and Security Patches
Another critical aspect of cybercrime prevention is regularly updating software and applying security patches. Cybercriminals exploit software vulnerabilities to gain unauthorized access to systems, making it vital to keep all software up to date.
- Importance of Updates:
- Bug Fixes: Software updates often include fixes for known vulnerabilities. Not applying these updates leaves systems at risk.
- New Features and Enhancements: Updates aren’t only about security; they also provide new features that enhance user experience and system functionality.
- Automated Updates: Many software applications allow for automatic updates, ensuring you always have the latest patches without needing to think about it. Enabling this feature can significantly enhance security.
- Regularly Check for Updates: For systems that don’t offer auto-updates, setting specific times to check for and install updates is crucial. Keeping your operating systems, applications, and anti-virus software current can further protect your digital environment.
Example: Take a scenario where a major health organization fell victim to a ransomware attack. The culprits had exploited an outdated version of a software application that had available patches. If the organization had prioritized updates, they might have avoided the significant financial and reputational loss that ensued.
Employee Training
One of the most effective ways to prevent cybercrime is through thorough employee training. Cybersecurity isn’t solely a technical issue; human factors play an essential role in maintaining security.
- Building Cybersecurity Awareness:
- Phishing Simulations: Conducting phishing simulation exercises helps employees recognize suspicious emails and learn how to respond appropriately.
- Best Practices: Training sessions should teach employees about the importance of password security, recognizing safe websites, and understanding social engineering tactics.
- Regular Updates and Refresher Courses: Cyber threats are ever-evolving, so offering regular training sessions ensures that employees are up to date with current scams and attacks.
Personal Anecdote: In a tech startup, employees had to attend regular cybersecurity workshops. During one training session, they were shown examples of phishing emails. The information helped one employee, Lisa, identify a phishing attempt that could have compromised company data. This proactive measure undoubtedly saved the company from potential harm.
In Summary
Implementing robust strategies for cybercrime prevention is pivotal in today’s digital landscape. Strong passwords and encryption provide a solid foundation, while software updates and employee training create a comprehensive approach to security. By taking these steps seriously, individuals and organizations can significantly reduce their risk of falling victim to the ever-evolving tactics of cybercriminals, paving the way for a safer online environment.

Investigation and Prosecution of Cybercrimes
As cybercrime continues to evolve, so too must the methods used to investigate and prosecute these offenses. Law enforcement agencies, digital forensics, and the legal system each play crucial roles in addressing the complexities of cybercrime. In this section, we will explore the roles of law enforcement agencies, the importance of digital forensics, and the legal challenges faced in prosecuting cybercriminals.
Role of Law Enforcement Agencies
Law enforcement agencies are on the front lines of combatting cybercrime. Their role is not just reactive; they are essential in preventing cyber incidents through proactive measures and collaborations.
- Investigation Teams: Many law enforcement agencies have specialized cybercrime units composed of trained investigators who understand both technology and criminal behavior. These units focus on various cyber offenses, ranging from identity theft to large-scale hacking incidents. They gather evidence, track suspects, and coordinate with other agencies.
- Collaboration: Given the international nature of many cybercrimes, collaboration is key. Agencies work together across borders through organizations like Interpol and Europol to share intelligence and track criminals operating globally.
- Public Awareness Campaigns: Many agencies partake in community outreach programs, educating the public about cybersecurity risks and safe online practices. For instance, annual events like Cybersecurity Awareness Month aim to empower citizens to protect their digital identities.
Personal Example: A friend of mine, Alex, was a victim of identity theft. After reporting it, he was pleasantly surprised by how quickly the local cybercrime unit took action. Their dedication and collaboration with other agencies resulted in the apprehension of the criminal and the restoration of Alex's stolen funds.
Digital Forensics
Digital forensics plays a critical role in the investigation of cybercrimes. The process involves the collection, preservation, and analysis of digital data to find evidence of criminal activity.
- Evidence Collection: Digital forensic experts know how to carefully collect evidence from devices like computers, smartphones, and servers. This process is meticulous, ensuring that no data is altered during collection.
- Data Analysis: Once collected, the data goes through a comprehensive analysis either to identify the perpetrator or to gather corroborative evidence for prosecution. Tools and software can help recover deleted files, track digital footprints, and analyze communication patterns.
- Reporting and Testimony: Forensics specialists also prepare detailed reports of their findings and may be called to testify in court as expert witnesses, translating complex technical jargon into understandable terms for jurors.
One notable case is that of a cyberstalking victim whose abuser was caught through meticulous digital forensic analysis. Experts retrieved deleted messages and location data that pointed directly to the perpetrator, leading to a successful conviction.
Legal Challenges
Despite the advancements in investigations and forensics, prosecuting cybercrimes poses unique legal challenges. The nature of digital evidence can complicate cases, and law enforcement must navigate a series of hurdles:
- Jurisdictional Issues: Cybercrime often spans multiple jurisdictions and countries, creating complications in law enforcement efforts. Different countries have varying laws, making it challenging to secure cooperation from foreign authorities.
- Evidentiary Complexities: Digital evidence can sometimes be viewed as less reliable than traditional evidence. Courts may not be familiar with the technical aspects of digital forensics, potentially complicating how evidence is presented.
- Rapidly Changing Laws: The legal landscape surrounding cybercrime is continuously evolving. New technologies often outpace existing laws, leaving gaps in regulations and enforcement capabilities. As a result, legal frameworks may struggle to keep up with the innovative tactics employed by cybercriminals.
In one case, an individual was charged with hacking into a corporation's system to steal data. However, the defense argued that the data was not adequately preserved, leading to a dismissal of key evidence. This scenario highlights the importance of following legal protocols in evidence handling.
In Summary
The investigation and prosecution of cybercrimes are vital in creating a safer digital environment. Law enforcement agencies, the integral role of digital forensics, and navigating legal challenges illustrate the complexity of this ongoing battle against cybercrime. Through collaboration, technical expertise, and a thorough understanding of the legal landscape, authorities can make strides in ensuring that cybercriminals are held accountable and that victims receive justice. As technology continues to advance, so too must our efforts to protect society from the unwelcome intrusion of cybercriminals.

International Cooperation in Combatting Cybercrime
As cybercrime transcends national borders, international cooperation has become essential in addressing this complex and growing issue. Cybercriminals often take advantage of the global nature of the Internet to undermine laws and exploit jurisdictions. To combat this, organizations like Interpol and Europol work tirelessly to coordinate efforts and facilitate information sharing among member countries. Additionally, international treaties like the United Nations Convention against Transnational Organized Crime play a crucial role in fostering collaboration. Let’s explore these entities and their impact on combating cybercrime.
Interpol
Interpol, or the International Criminal Police Organization, is one of the most recognized international police organizations, dedicated to facilitating cooperation and collaboration among member countries in crime prevention and investigation.
- Global Reach: Interpol serves 195 member countries, providing a platform for sharing information and data related to criminal activities, including cybercrime. The organization's centralized database of criminal information plays a vital role in tracking suspects and sharing intelligence.
- Cybercrime Units: Interpol has specialized cybercrime units that focus on developing strategies, conducting training, and sharing best practices among law enforcement agencies worldwide. These units assist countries in responding to cyber threats and emerging criminal methods.
- Operations and Campaigns: Interpol frequently runs operations to combat cybercrime, such as Operation Lyrebird, which targeted online child exploitation. Such operations demonstrate the importance of global vigilance in addressing specific cyber threats.
Personal Example: I recall reading about how a collaborative effort led by Interpol helped apprehend a notorious hacker involved in identity theft across several continents. This operation showcased how vital it is to harness international cooperation in the digital age.
Europol
Europol, the European Union's law enforcement agency, plays a significant role in combating cybercrime within Europe and beyond. Its primary mission is to support member states in their fight against serious crime, including cyber threats.
- European Cybercrime Centre (EC3): Established within Europol, EC3 works to enhance the capabilities of member states to counter cybercrime. It promotes information sharing, provides analytical support, and conducts coordinated operations against cybercriminals.
- Collaboration with Private Sector: Europol doesn’t just work with law enforcement agencies; it also collaborates with private sector entities. By partnering with technology companies, Europol can gain insights into emerging cyber threats, share intelligence, and develop preventative measures.
- Public Awareness Initiatives: Europol actively seeks to educate the public about cyber safety. Their campaigns often involve awareness-raising activities to help individuals and organizations recognize and avoid cyber threats, fostering a culture of cybersecurity.
For instance, a joint operation between Europol and several member states successfully dismantled a criminal network involved in distributing malware. The collaboration among countries resulted in significant arrests and emphasized the need for collective action.
United Nations Convention against Transnational Organized Crime
The United Nations Convention against Transnational Organized Crime provides a legal framework that facilitates international cooperation in combating various forms of organized crime, including cybercrime.
- International Legal Standards: This convention sets forth legal standards that help harmonize laws and practices among nations, making it easier for countries to collaborate on investigations and prosecutions related to cybercriminal activities.
- Protocol Against the Transfer of Technology: Within the convention, specific protocols address the illegal transfer of technology used for criminal purposes. This helps countries establish regulatory frameworks to prevent and respond to cybercrime effectively.
- Capacity Building: The UN also focuses on strengthening the capabilities of countries to tackle cybercrime through training and resources. By empowering local law enforcement and judicial authorities, the convention promotes a global fight against organized crime.
Example: One notable success stemming from the collaboration under this convention involved a network engaged in human trafficking and online exploitation. The legal framework empowered multiple countries to cooperate and dismantle the operation, demonstrating the importance of international unity in tackling complex crimes.
In Summary
International cooperation is crucial in the ongoing effort to combat cybercrime effectively. Through organizations like Interpol and Europol, as well as frameworks established by the United Nations Convention against Transnational Organized Crime, countries can work together to address this borderless threat. As cybercriminals continuously adapt and innovate their tactics, robust international partnerships will remain essential in ensuring a coordinated response to these challenges, ultimately making the online world a safer place for everyone.
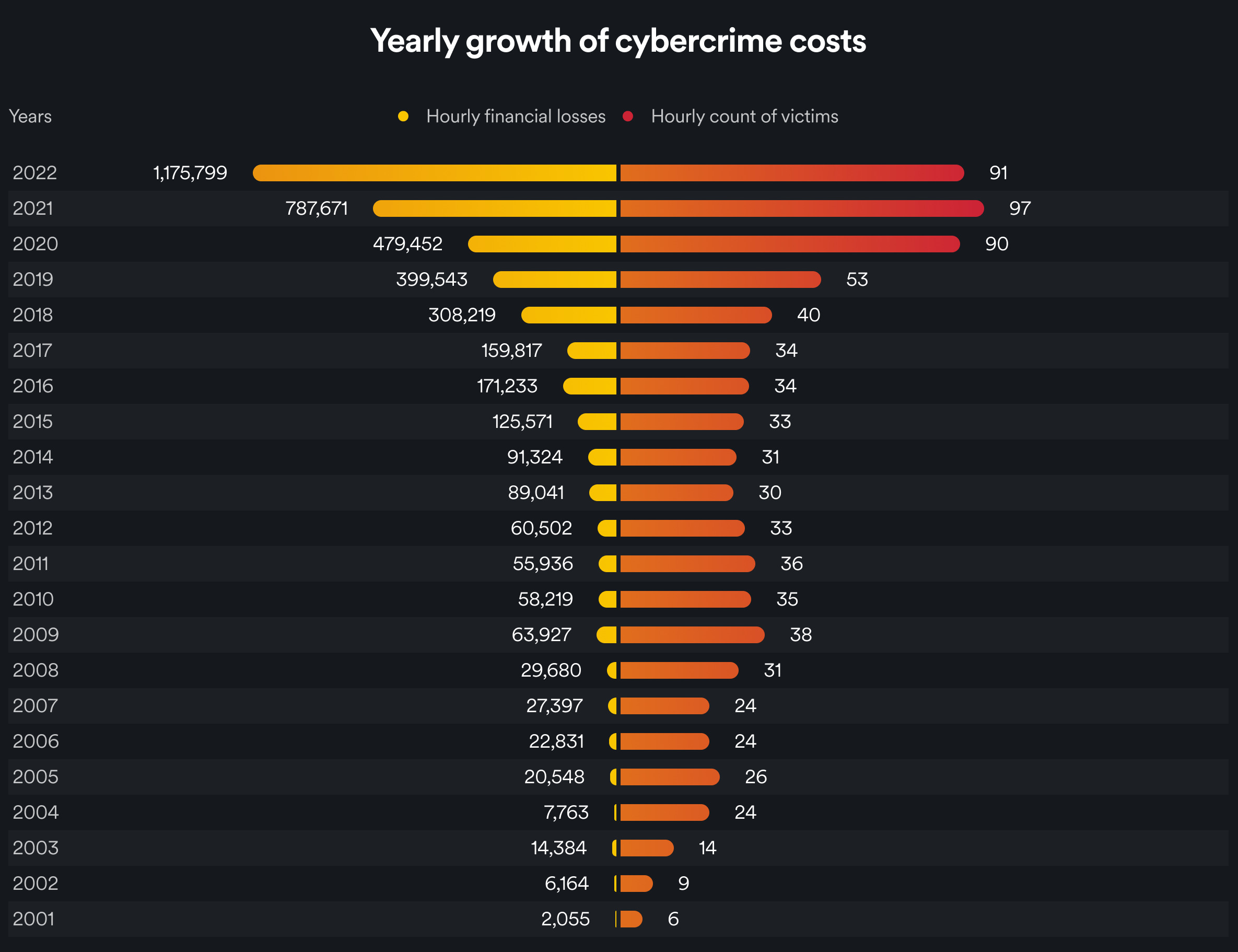
Future Trends in Cybercrime
As technology continues to advance at a rapid pace, so do the threats and trends in cybercrime. Understanding these emerging trends is critical for both individuals and organizations looking to safeguard their digital assets and maintain security in an increasingly interconnected world. In this section, we'll explore three significant trends: the impact of artificial intelligence and machine learning on cybercrime, the vulnerabilities posed by the Internet of Things (IoT), and the rise of cyber warfare.
Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning are reshaping the landscape of both cybersecurity and cybercrime. While these technologies can be harnessed for protective purposes, they also offer new tools for cybercriminals.
- Offensive Use of AI: Criminals can leverage AI to execute attacks more effectively. For example, AI-driven algorithms can be employed to automate phishing schemes, making phishing emails appear more authentic and personalized. This increases the likelihood that unsuspecting users will fall victim.
- Deepfakes and Misinformation: The rise of deepfake technology, which uses AI to create realistic fake videos and audio, poses a unique challenge. Cybercriminals can exploit deepfakes for disinformation campaigns, blackmail, and reputation damage by impersonating individuals.
- Automated Attacks: AI can also be used to develop sophisticated malware that can adapt and evade detection, making traditional cybersecurity measures less effective. This arms race between cybercriminals and security professionals could escalate in the coming years.
Personal Anecdote: A friend in the cybersecurity field shared an alarming incident where a company faced significant losses due to a deepfake video that falsely portrayed their CEO making controversial statements. The incident was a reminder of how rapidly technology can be exploited for malicious purposes.
Internet of Things (IoT) Vulnerabilities
The rapid proliferation of Internet-connected devices, known as the Internet of Things (IoT), presents a new frontier for cybercriminals. With more devices connected to the internet than ever before, vulnerabilities in these devices can open the door to various cyber threats.
- Insecure Devices: Many IoT devices are designed with convenience in mind but often lack robust security features. As a result, they can be easily hacked, allowing attackers to gain access to users' networks.
- Botnets: Compromised IoT devices can be hijacked to form large botnets, which are networks of hijacked devices used for distributed denial-of-service (DDoS) attacks. This trend has already been seen in instances like the Mirai botnet, which leveraged IoT devices to launch devastating attacks on internet infrastructure.
- Home Automation Security Risks: As more households adopt smart devices, the potential for cyber breaches increases. Hackers can exploit weaknesses in devices like smart cameras, thermostats, and even refrigerators, raising concerns about privacy and security.
Example: In a recent case, a couple noticed unusual behavior in their smart thermostat and security cameras. After investigating, they discovered that their devices had been compromised and were leaking personal information to unauthorized users. This incident highlighted the urgent need for stronger security protocols for IoT products.
Cyber Warfare
Cyber warfare is emerging as a significant trend in the realm of national security. Countries are increasingly using cyber capabilities to disrupt the infrastructure of rival nations, engage in espionage, and destabilize political systems.
- State-Sponsored Attacks: Governments are investing heavily in cyber capabilities, resulting in a surge of state-sponsored attacks against critical infrastructure, financial systems, and public services. This trend could lead to escalating tensions between nations and introduce new risks to global cybersecurity.
- Targeting Critical Infrastructure: Cybercriminals may aim for vital sectors such as power grids, healthcare systems, and transportation networks. A successful attack on these systems could lead to chaos and significant loss of life, emphasizing the severity of cyber warfare.
- Propaganda and Misinformation: Cyber warfare often includes the use of disinformation campaigns to manipulate public opinion and sow discord among populations. Hackers may exploit social media platforms to spread propaganda or create division.
Example: Consider the incident in which a foreign state launched cyberattacks against hospitals during a pandemic, causing significant disruptions. This event underlined how cyber warfare affects not just nations but individual lives, making it a pressing concern for national security departments.
In Summary
The future trends in cybercrime highlight a complex landscape shaped by technological advancements and a rapidly changing digital environment. As artificial intelligence enhances the capabilities of cybercriminals, IoT vulnerabilities expose personal and organizational data, and cyber warfare escalates tensions between nations, it’s crucial to remain vigilant. Individuals and organizations must adapt to these trends by implementing robust cybersecurity measures, fostering awareness, and collaborating globally to mitigate risks. Ultimately, the ongoing evolution of cybercrime demands proactive action and a commitment to staying informed and prepared in a digitally connected world.

Conclusion and Recommendations
As we draw our exploration of cybercrime to a close, it’s essential to reflect on the critical themes and insights that emerged throughout our discussion. The ever-evolving landscape of cybercrime presents real challenges for individuals and organizations alike. However, understanding these challenges and implementing proactive strategies can make a significant difference in safeguarding digital assets. Let’s summarize the key points and offer some recommended actions to enhance cybersecurity.
Summary of Key Points
Throughout our discussion, we’ve covered various facets of cybercrime, highlighting its complexity and multidimensional nature:
- Types of Cybercrime: From identity theft and phishing attacks to ransomware and malware distribution, the methods employed by cybercriminals are diverse and impact businesses and individuals on multiple fronts.
- Impact of Cybercrime: The financial losses, reputational damage, and legal repercussions from cyber incidents can be significant. Organizations may suffer long-term consequences that affect their viability and require substantial recovery efforts.
- Prevention Strategies: By employing robust cybersecurity measures, businesses and individuals can help protect themselves from cyber threats. These include strong passwords, regular software updates, and employee training.
- Investigation and Prosecution: Understanding how law enforcement agencies investigate cybercrimes, coupled with the importance of digital forensics, reveals the complexity and challenges in prosecuting offenders.
- International Cooperation: Organizations like Interpol and Europol underline the necessity for global collaboration in combatting cybercrime, which transcends national boundaries.
- Future Trends: The rise of artificial intelligence, vulnerabilities in IoT devices, and the emergence of cyber warfare represent critical areas for which individuals and companies need to prepare.
With this overview in mind, the landscape may seem daunting, but there are ways to enhance resilience against cybercrime.
Tips for Protecting Against Cybercrime
Here are some practical recommendations that can help individuals and organizations bolster their defenses against cyber threats:
- Strengthen Passwords:
- Use complex passwords that include a mix of letters, numbers, and symbols.
- Consider using a password manager to generate and store unique passwords for different accounts.
- Implement Two-Factor Authentication (2FA):
- By requiring two forms of identification to access accounts, 2FA adds a crucial layer of security. For example, using a mobile app to generate a one-time code can significantly reduce the risk of unauthorized access.
- Regularly Update Software:
- Make it a habit to install software updates and security patches promptly. This practice helps eliminate vulnerabilities that cybercriminals might exploit.
- Educate Yourself and Employees:
- Ongoing training about common cyber threats, such as phishing scams and social engineering tactics, can empower individuals to recognize and report suspicious activity. Consider organizing regular cybersecurity workshops or seminars.
- Backup Important Data:
- Regularly back up your data to secure locations, whether it be cloud storage or external hard drives. In the event of a ransomware attack, having backups can reduce the impact significantly.
- Use Firewall and Antivirus Protection:
- Ensure that your devices are equipped with reliable firewall and antivirus software. This can help detect and prevent malware before it has a chance to disrupt your system.
- Stay Informed:
- Continuously seek information about new threats and cyber trends. Subscribing to reputable cybersecurity blogs or newsletters can help keep you updated on the latest developments.
Final Thoughts
In conclusion, while the threat of cybercrime is growing and becoming more sophisticated, it is not insurmountable. By understanding the risks, implementing robust security measures, and fostering a culture of awareness, individuals and organizations can protect themselves against cyber threats. Cybersecurity isn’t just the responsibility of IT departments—it’s a shared commitment that everyone must embrace. As we look ahead to an evolving digital landscape, being prepared is our best defense against cybercrime. With proactive measures, education, and cooperation, we can navigate the complexities of cyber challenges and enhance the safety of our digital lives.
